I recently deployed Cisco Amp For Endpoints to a few CentOS 6 and 7 servers. After installation, I noticed that the dashboard showed no ClamAV updates. I let each one sit overnight, but returned to the same status.
To solve “Definitions Last Updated: None,” assuming there is no connectivity issue to the ClamAV servers, restart the connector services as shown below. However, be sure to verify ping, DNS resolution, and port 80/443 tests to the server listed in the dashboard.
Utilize logs in /var/log/cisco and tools in /opt/cisco/amp/bin to help troubleshoot and resolve the issue.
Step 1
Identify if there’s an issue. Go to the dashboard and find the servers. You’ll probably see an orange alert that definitions haven’t been updated.
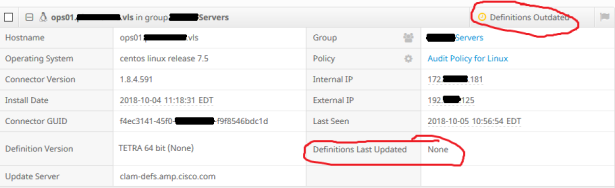
The AMP For Endpoints dashboard shows that ClamAV definitions have never been updated.
Step 2
There are several log files in /var/log/cisco that can provide additional service information.
CentOS 7
[root@ops01~]# systemctl list-unit-files | grep amp cisco-amp.service enabled cisco-ampmon.service disabled cisco-ampupdater.service disabled [root@ops01~]# systemctl restart cisco-ampupdater.service [root@ops01~]# systemctl restart cisco-amp.service [root@ops01~]# cd /opt/cisco/amp/bin [root@ops01 bin]# ls ampcli ampmon ampservice ampsupport cisco-amp-helper libclammspack.so.0 libclamunrar_iface.so libclamunrar_iface.so.7.1.1 libclamunrar.so.7 libmnl.so libmnl.so.0.2.0 ampdaemon ampscansvc ampsigncheck ampupdater libclammspack.so libclammspack.so.0.1.0 libclamunrar_iface.so.7 libclamunrar.so libclamunrar.so.7.1.1 libmnl.so.0 modules [root@ops01 bin]# ./ampupdater [root@ops01 bin]#
CentOS 6
[root@ops01]# less ampdaemon.log Oct 22 15:51:41 NETFLOW ampdaemon[4427] [ui]:[notice]-[ui_comms.c@1476]:[139769633826560]: UI connection on socket 29 allows privileged commands Oct 22 16:00:30 NETFLOW ampdaemon[4427] [air_libs]:[error]-[fa_cloud_async.c@670]:[139769602356992]: _fa_async_handle_response(): received stale or superfluous response: sessid=0 txid=55 [root@ops01]# less ampupdater.log Oct 22 15:51:31 NETFLOW [4619] [config]:[info]-[config.c@944]:[140238088169440]: xpath /config/updater/lastmod does not exist or is empty Oct 22 15:51:31 NETFLOW [4619] [config]:[info]-[config.c@944]:[140238088169440]: xpath /config/updater/server does not exist or is empty Oct 22 15:51:31 NETFLOW [4619] [updater]:[info]-[updater.c@130]:[140238088169440]: no update server present [root@NETFLOW bin]# cd /etc/init/ [root@NETFLOW init]# ls | grep amp cisco-amp.conf cisco-ampmon.conf cisco-ampupdater.conf [root@NETFLOW init.d]# initctl stop cisco-amp cisco-amp stop/waiting [root@NETFLOW init.d]# initctl start cisco-amp cisco-amp start/running, process 25542 [root@NETFLOW init.d]# initctl status cisco-amp cisco-amp start/running, process 25542 [root@NETFLOW init]# initctl status cisco-ampupdater cisco-ampupdater stop/waiting [root@NETFLOW init]# initctl start cisco-ampupdater cisco-ampupdater stop/waiting
Step 3
Wait 5-10 minutes, then check/force sync policies.
[root@ops01 bin]# ./ampcli Trying to connect... Connected. ampcli> help scan Initiate/pause/stop a scan * See 'scan help' for more. status Get ampdaemon status sync Sync policy policy Show policy exclusions List custom exclusions history Show event history * See 'history help' for more. quarantine List/restore quarantined file(s) * See 'quarantine help' for more. about About AMP for Endpoints Connector notify Toggle notifications verbose Toggle verbose mode q Quit ampcli interactive mode ampcli> history list Date Event Details ================================================================================= | 2018-10-05 10:37 AM | Definition Update | ID:128 known viruses:6670463 | | | version:25009 cloud:0 local:4 | | | official:4 type:CVD (Update succeeded) … ================================================================================= [ Page 1 of 1 (total results: 5) ] ampcli> sync Request sent to sync policy to latest version ampcli> policy Quarantine Behavior: Do not quarantine malicious files. Protection: Monitor program install. Monitor program start. Passive on-execute mode. Proxy: NONE Notifications: Do not display cloud notifications. Policy: Audit Policy for Linux (#149) Last Updated: 2018-10-05 11:06 AM
Step 4
Wait a few more minutes, then check the AMP dashboard.
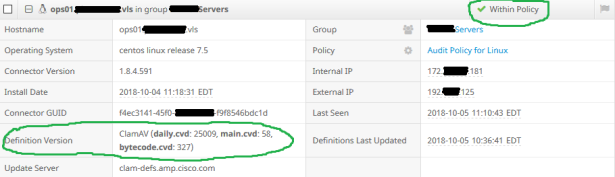
The AMP For Endpoints dashboard shows that ClamAV definitions are now successful.
Step 5
If needed, check the logs in /var/log/cisco.
If you see errors such as:
Oct 5 10:35:40 ops01....vls ampdaemon[16018] [cvd_update]:[error]-[hb_clam.c@2064]:[139886856197888]: Unable to access file so using default time of 0 for /opt/cisco/amp/etc/clamav/main.cvd: No such file or directory
These should have been resolved by the above steps.
If you’re still having issues, open a support case and generate troubleshooting info.
[root@ops01 bin]# ./ampsupport [logger] Set minimum reported log level to notice date uname -a hostname … … semodule -l total 3768359, actual 3768359 Saved the support package to: /root/Desktop/AMP_Support_2018_10_05_15_15_07.zip [logger] Shutdown file logger for module: [root@ops01 bin]#
Conclusion
There might be a more succinct way to troubleshoot and resolve this issue, but this is the process that worked reliably for me. I haven’t exactly pinned down why a simple service restart is necessary on first install, but it’s an easy fix.